XSS and SQLi in Forecast® by Tideworks
Tideworks: CVE-2022-43112 & CVE-2022-43115: Forecast® (10.10.0.13153)
Tideworks' Forecast® application serves as a method for terminals to establish communication with various parties within the industry, such as shipping lines and trucking companies, or other terminals around the globe. The application is designed to reduce overall costs and improve gate turn times for participating terminals. Black Lantern Security (BLS) operators identified an unauthenticated SQL injection vulnerability in the `companyType` parameter during the self registration flow. This injection was leveraged to obtain Forecast® user session cookies which were used to login to the application with administrative privileges, ultimately resulting in operators uncovering additional findings.
CVE-2022-43115 - Error-Based SQL Injection
During the self-registration process, customers are asked to provide their type of company, whether it be a shipping company, trucking company, etc. This information is then checked against the backend database to determine how the new user will proceed with registration. While enumerating this functionality, BLS operators discovered that the `companyType` parameter was being used in a SQL statement due to Oracle Database error messages appearing in HTTP responses when providing crafted inputs. Operators were then able to break out of the original SQL query using traditional SQL injection methods to extract data from the database. Operators used the Oracle Database errors as an advantage for quick data retrieval, due to query results being displayed in the error messages themselves. For example, the following query could be used to break out of the original query and obtain results within the error messages:
CO_BROKER_FORWARDING'||(SELECT CTXSYS.SN(user,(SELECT banner FROM
v$version WHERE rownum=1)) FROM dual)||'With the ability to read the values stored in the database, BLS operators opted to use SQLMap to quickly dump targeted information in search of a privilege escalation avenue. After some additional database enumeration, operators discovered a particular table home to columns storing user session cookies (`JSESSIONID`), as well as dates and times of when the associated session cookies were written to the database. Armed with this knowledge, operators executed customized queries aimed to pull valid session cookies from the database based on the date they were created. For example, pulling up to 100 `JSESSIONID` cookies that were created on 27 May 2022 would look like the following:
SELECT session_id FROM FORECAST_REST_LOG WHERE start_request LIKE '%27-MAY-22' AND rownum <=100After pulling down a list of `JSESSIONID` cookies, operators were able to copy the cookie value into a browser to ride the currently logged on user. From an attacker's perspective, there was little control over which user sessions were returned however, repeated exploitation yielded a high chance of obtaining an administrator session. This is due to the likelihood of various users logging into the application and creating a new session every day. Once successfully authenticated with an admin session, BLS operators were led to the discovery of several other areas of flawed input validation. These included an additional error-based SQL injection, and several areas affected by reflected and stored XSS (CVE-2022-43112) which could be utilized by an attacker for advanced phishing campaigns or other nefarious actions.
CVE-2022-43112 - XSS (Multiple)
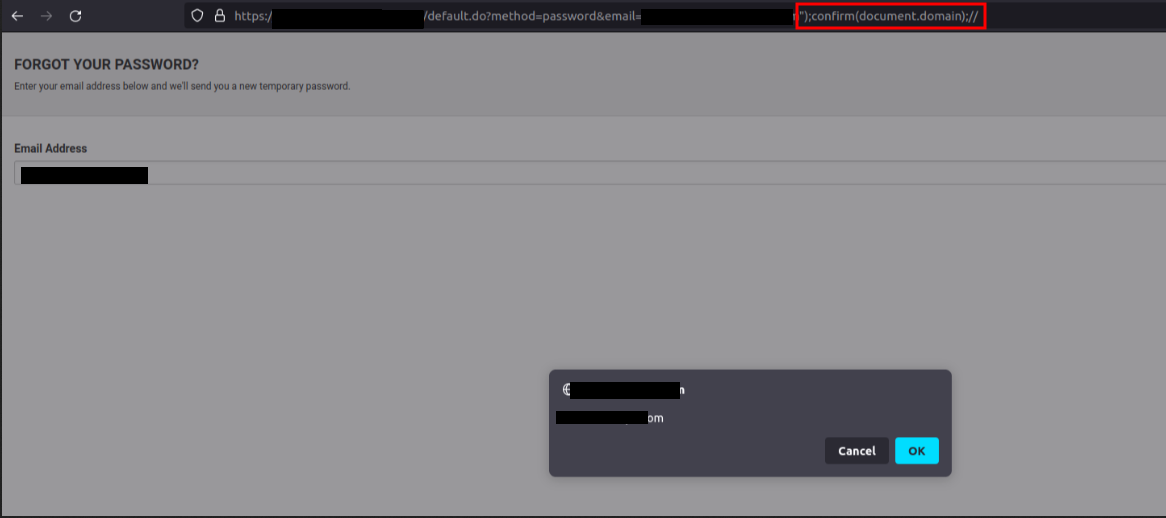
After gathering a thorough understanding of the application, along with newly acquired privileges, BLS operators managed to uncover several additional input validation flaws. These included an unauthenticated reflected XSS occurring within the `email` GET parameter when attempting to send a password reset email, an authenticated reflected XSS within the `vesselVoyageName` GET parameter allowing JavaScript execution when generating a booking discrepancy report, and lastly an authenticated stored XSS was discovered within the `Notes` section of user profile pages.
Upon the identification of the aforementioned vulnerabilities, along with an understanding of the criticality of the application, BLS operators stopped conducting activity against the application and alerted our client to the vulnerabilities. After initial discussion with the client, BLS reached out to Tideworks to inform them of the issues.
Tideworks kept an open line of communication informing BLS of swift and effective remediations toward the discovered findings. During the time the vulnerabilities were announced to Tideworks, the Forecast® application version was `10.10.0.13153 (10152021-0328)`. Tideworks has rolled out major updates remediating the affected resources in version `10.10.0.13669 (08292022-2313)` of the application. Port authorities and other parties in the industry utilizing Forecast® by Tideworks should ensure the latest update has been deployed within their production environment.