Reflected XSS in AEM ACS Commons Version 5.1.x and Earlier
AEM ACS Commons: CVE-2022-28820: Version 5.1.x
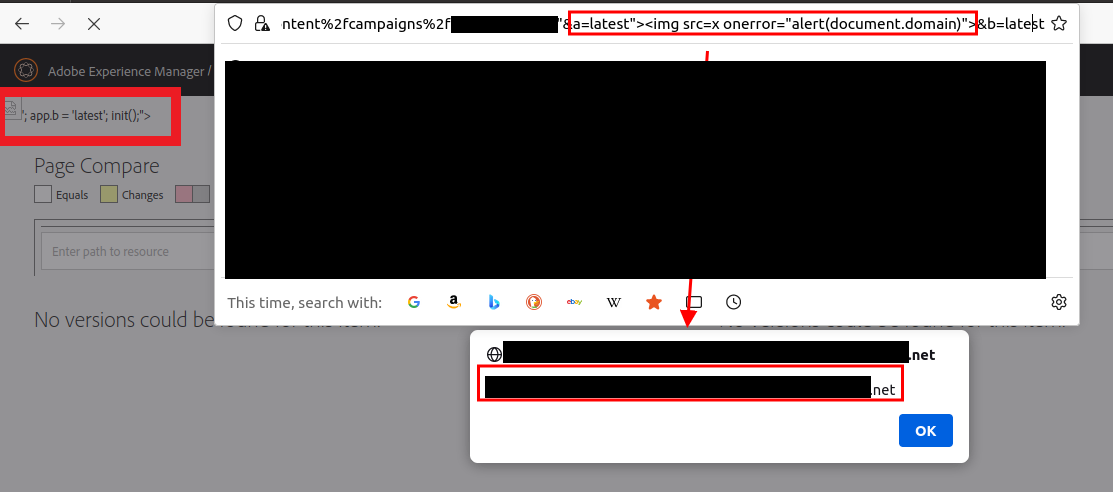
While testing an instance of the Adobe Experience Manager (AEM) web application suite for one of our customers, BLS operators discovered reflected cross-site scripting vulnerability in the AEM’s “author” application’s page compare functionality, accessible via the endpoint /apps/acs-commons/content/page-compare.html.
The endpoint is vulnerable via the a and b GET parameters. User input submitted via these parameters is rendered directly into the HTTP response without validation or sanitization. As a result, arbitrary JavaScript code is executed in the victim's browser.
When an authenticated user visits the following URL the embedded XSS payload will execute.
https://<AEM instance domain>/apps/acs-commons/content/page-compare.html?path=%2fcontent%2fcampaigns%2ftest%22&a=latest%22%3E%3Cimg%20src=x%20onerror=%22alert(document.domain)%22%3E&b=latest
In this case, the payload is a benign call to alert(document.domain), which serves to validate the vulnerability and prove access to the page's document object model (DOM).
The vulnerable component was identified to be in the Adobe-managed open-source library ACS AEM Commons, in version 5.1.x and earlier. The project is a dependency used by some administrative functionality used with Adobe Experience Manager platform.
The issue was assigned CVE-2022-28820 and was patched in version 5.20 of ACS AEM Commons. The root cause was a missing call to an encoding function that had been applied elsewhere within the library.
It appears the issue may have been independently discovered previously and assigned CVE-2021-21043, and an incomplete/ineffective fix was potentially applied.