Privileged Read and Weak Default Credentials in Brocade Fabric OS
Brocade: CVE-2021-27796, CVE-2021-27797: Fabric OS (Multiple Versions)
Brocade Fabric OS is used for monitoring physical, protocol, and application layer data points of a storage area network (SAN) in real time. Black Lantern Security (BLS) identified multiple vulnerabilities including the ability to read files with privileged permissions (root) as well as weak default credentials. The combination of the two vulnerabilities allows an attacker to read any file on the affected system.
CVE-2021-27797 - Hard Coded Credentials
Brocade Fabric OS v8.2.1c, v8.1.2h, v8.0.x, and v7.x shipped with default accounts and passwords in place. These accounts, such as "user" and "factory", are configured to accept "password" for authentication. It was instructed per documentation that these credentials should be changed, however administrators were able to bypass the prompt to change the password. An attacker can simply connect to the vulnerable systems using SSH and gain access to a restricted shell environment (rbash).
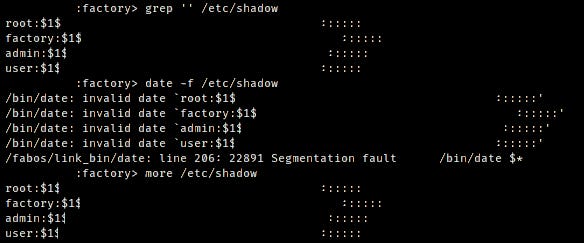
CVE-2021-27796 - Authenticated Privileged File Read
Brocade Fabric OS <8.0.1b and <7.4.1d was discovered to have an authenticated privileged file read vulnerability. Utilizing the previous vulnerability, an authenticated attacker has access to binaries within rbash that can be abused to read off the file contents of arbitrary files. Binaries used include date, grep, and more for the factory user. Additionally, the account user is able to abuse binaries grep and more.
Remediation
Brocade SIRT was notified of these vulnerabilities and has since issued the following solutions:
CVE-2021-27796
Upgrade to relevant versions
v9.0.0,v8.0.1b,v7.4.2,v8.0.2,v7.4.1d, which have received a security update for this issue
CVE-2021-27797
Upgrade to relevant versions
v9.0.0,v8.2.1c,v8.1.2h, and higher, which have received a security update for this issueAdditionally, update the credentials set for the default accounts from
passwordto something secure