NASCENT RemKon Multiple CVEs
NASCENT: CVE-2021-38611, CVE-2021-38612, CVE-2021-38613: RemKon Device Manager 4.0.0.0
NASCENT’s RemKon Device Manager is a web application that is deployed in logistic centers to serve as a “single pane of glass” for the management of various settings and configurations for Automated Gate Systems (AGS) and other NASCENT products. Black Lantern Security (BLS) identified a total of 3 CVEs for this software during a customer engagement. CVE-2021-38611 allows for the execution of arbitrary commands during a file upload, CVE-2021-38612 is a directory traversal vulnerability, and CVE-2021-38613 allows for the upload of arbitrary files. Authentication is not required by default for this software.
CVE-2021-38611 and CVE-2021-38613
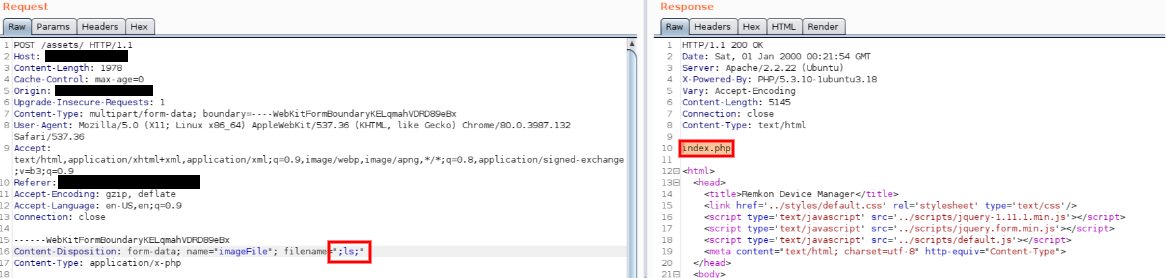
The RemKon Device Manager image upload function executes system commands to store uploaded files in /tmp. Due to this code using raw system commands with no filtering of user input, an attacker can append a semi colon to a file name in order to escape this function and execute arbitrary system commands. The arbitrary command execution vulnerability was assigned the ID CVE-2021-38611.
Additionally, this PHP function does not perform any file type validation. Fortunately, as stated previously, uploaded files are stored in /tmp, so web shells are not able to be immediately accessed when this functionality is abused (but this concern is largely rendered moot with CVE-2021-38611). The arbitrary file upload was assigned the ID CVE-2021-38613.
CVE-2021-38612
The RemKon Device Manager also features a log reading function that does not sanitize user input, allowing an attacker to read files on the underlying server (including source code for the web application). The directory traversal vulnerability was assigned the ID CVE-2021-38612.
NASCENT was informed regarding the nature of these vulnerabilities shortly after their discovery. The newest version of the RemKon Device Manager remediates the identified issues.