Mapping Windows Audit Log Settings to MITRE Data Sources for Rabobank-CDC DeTT&CT
Use the DeTT&CT framework to assess TTP coverage, perform gap analysis, and prioritize detection engineering efforts
References
https://attack.mitre.org/
https://github.com/rabobank-cdc/DeTTECT
https://github.com/rabobank-cdc/DeTTECT/wiki/Data-quality
https://github.com/rabobank-cdc/DeTTECT/wiki/Visibility-scoring
https://github.com/rabobank-cdc/DeTTECT/wiki/Detection-scoring
https://mitre-attack.github.io/attack-navigator/
https://rabobank-cdc.github.io/dettect-editor
https://github.com/blacklanternsecurity/blue-resources/blob/main/Windows_MITRE_Data_Source_Mapping.xlsx
One of the objectives for the initial phase of a risk assessment is to identify and analyze critical business workflows, as well as the IT assets and personnel that support them. Keep in mind that these workflows may not even be IT-specific. For example, consider the workflows associated with accounts payable, accounts receivable, vendor management, and treasury operations. What's important to understand is that critical workflows have the greatest potential risk. A successful attack on the IT assets, personnel, or data that support these workflows would result in significant negative impacts to the organization. The impact to an organization can be reduced by ensuring that critical IT assets and personnel are adequately defended. Administrative-, network-, host-, and email-based security controls can be strategically deployed to defend critical assets, personnel, and the workflows that they support.
In the event of an incident or breach, it is equally important to ensure that the data sources these security controls rely on are available, accurate, and provide the required fidelity. For example, if the aim is to detect and alert on brute force login attempts and the target server is not configured to log failed login attempts, then it will be incredibly difficult to detect the attack and isolate the attacker. An easy mental checklist might be:
Is the activity visible in your environment and does it generate any logging artifacts?
If so, where is the event being logged? What is the data source for that event?
Are the logs for that data source being shipped to a SIEM or centralized log management solution?
If so, is there an alert being generated when executing the attack?
Finally, are SOC analysts triaging the alert based on criticality?
This approach quickly becomes more complicated and resource-intensive as more and more attacks are considered. The MITRE Enterprise ATT&CK matrix currently includes 14 tactics, 191 techniques, and 385 sub-techniques. "MITRE ATT&CK® is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community." [1]
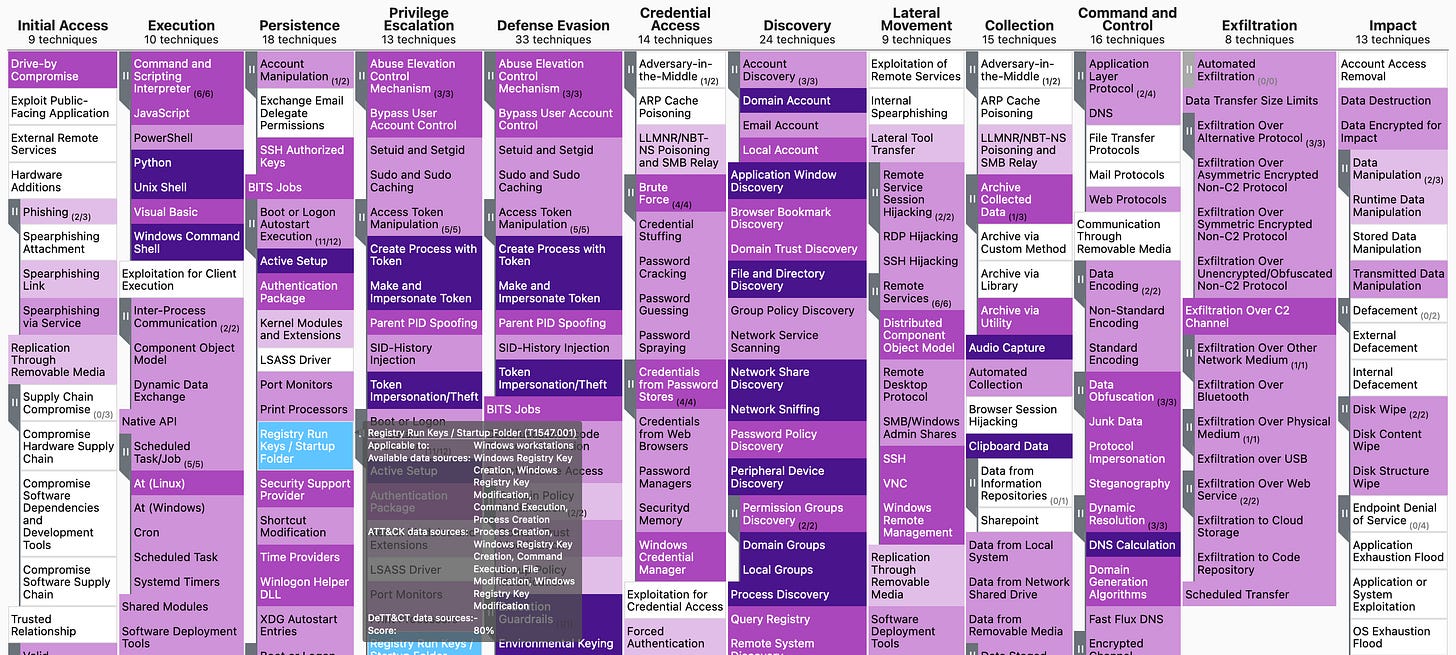
As a defender, a primary concern might be how much "coverage" an organization has for the tactics, techniques, and procedures (TTPs) detailed in the MITRE ATT&CK matrix. That is, based on existing security controls and data sources, what percentage of TTPs can I potentially detect? To make it easier for defenders to determine their current "coverage" for MITRE ATT&CK TTPs, the DeTT&CT [2] project has mapped attacker (sub)techniques to the data sources that should capture specific attacker activities. Therefore, as a first approximation, if a defender has one or more data sources configured and available, then they have the "potential" to detect the (sub)techniques that map to those data sources. Going from a potential detection to an actual detection depends on the completeness and quality of the data contained in each data source, as well as the number of data sources that could potentially capture activity surrounding a TTP.
The DeTT&CT framework provides defenders with a means to specify and score: - Data Sources - Data Quality - Visibility - Detection
Data quality is scored based on "device completeness, data field completeness, timeliness, consistency and retention" [3]. Visibility scores will depend on how many aspects of the attacker (sub)technique can be captured [4]. Theoretically, multiple high quality data sources should be configured for each (sub)technique. A Detection will be scored based on multiple factors including, timing, (sub)technique coverage, opportunities to bypass, false negatives, and false positives [5]. Data Source, Data Quality, Visibility, and Detection metrics can be visualized as ATT&CK Navigator layer files [6] that serve to illustrate an organization’s defensive posture. Establishing and increasing an organization's coverage is a continuous and resource-intensive process.
For the purposes of this post, the objective will be to generate a simple ATT&CK Navigator layer file that a defender can use to illustrate MITRE ATT&CK coverage for Windows systems based on data sources alone; data quality, visibility, and detections will not be considered for now. This basic coverage data can then be used as an input for assessing organizational risk.
The primary inputs for the MITRE Navigator file are the data sources that are available within the organization. However, the Rabobank-CDC DeTT&CT framework doesn't map the data sources to well known Windows Event Logs. In this case, it's left to the analyst to perform that mapping by hand. To that end, Adeem Mawani and Brian O'Hara have created a helpful worksheet published in the BLS Blue Team Resources Github repository [8]. The worksheet details each Windows Advanced Audit Log Setting and then maps that setting and its corresponding Windows Event IDs to its MITRE data source. Each entry includes:
Category
Subcategory
Default configuration
Baseline configuration recommendations
Conditions (success/failure)
MITRE data source name
MITRE data source ID
Windows event ID
Windows event description
The intention is to provide the analyst with a rubric for mapping the output of the auditpol command to actual MITRE data sources. Armed with a list of MITRE data sources, the MITRE Navigator layer file can be created. The end result is a map of "potential" coverage for MITRE ATT&CK TTP's based on available data sources.
The DeTT&CT Editor [7] is publicly hosted or can be run locally using:
python dettect.py editorIn the editor, create a new YAML file to store your available data sources:
Determine available data sources in your environment. For example, by using the published worksheet to map data sources to Windows audit log configurations:
Add applicable data sources using the interface at the bottom of the page:
Click "Save YAML file" to export your data sources
Run the following command to generate a navigator layer file using the exported YAML:
python dettect.py ds -fd data-sources.yaml -lView the ATT&CK Navigator using the following link to disable yellow underlines: https://mitre-attack.github.io/attack-navigator/#comment_underline=false
In Navigator, click "Open Existing Layer" and open the exported JSON layer file created from earlier.









Hadn't seen the detect framework before good stuff