Introducing CloudCheck: Comprehensive Cloud Provider Detection
An overhaul of BBOT's cloud detection
Cloud provider detection is an important part of most OSINT-related workflows. Whether for bug bounties, pentests, or Attack Surface Management (ASM), it’s useful to know, for example, which cloud providers your target likes to use, and whether the web app you’re about to hack is protected by a web application firewall (WAF) like Cloudflare.
Good cloud detection requires tracking domains and subnets owned by cloud providers. This is inherently difficult, since they’re constantly changing. Some providers, like Cloudflare, are kind enough to publish their ranges, which can be periodically scraped and aggregated into a combined signature. You can then check a host against those subnets to definitively answer the question, “Is this thing behind Cloudflare?”
But most providers don’t publish their infrastructure. This almost always leads to manual tracking of CIDRs, ASN numbers, and domains, and quickly devolves into a mess. Since the data must be scraped from multiple and/or competing sources — an HTML webpage here, a random person’s github there — it leads not only to outdated data, but incomplete and inaccurate data as well.
Here are some tools that helped to pioneer this capability, but which still rely on hardcoded lists:
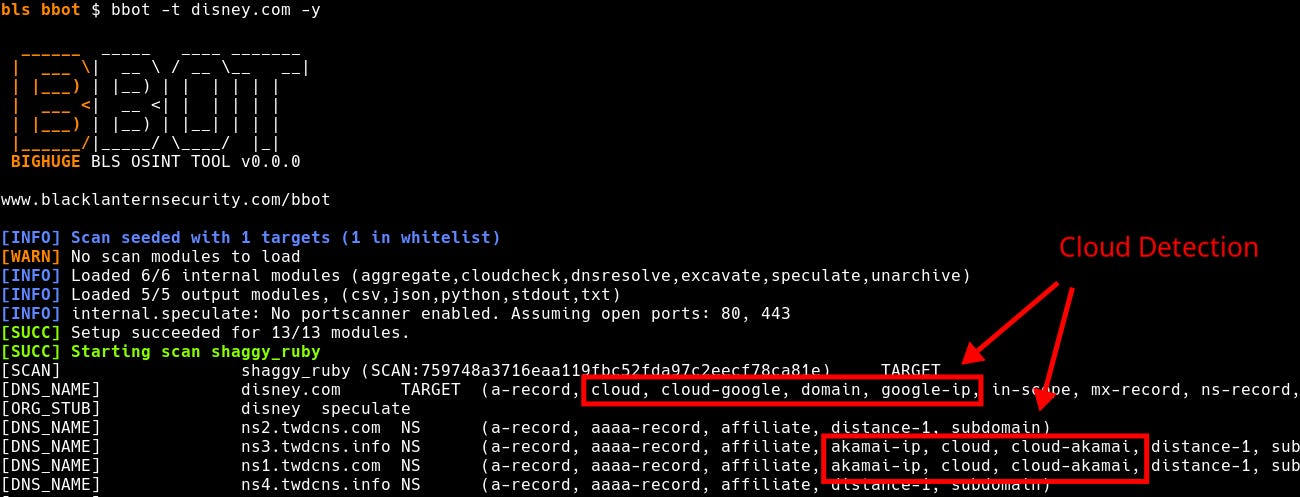
Basic cloud provider detection has always been built into BBOT. When you run a BBOT scan, hosts are tagged as “cloudflare”, “fastly”, etc:
Until today, BBOT’s CloudCheck-powered cloud detection has also relied on these same manual methods. This is why we’ve overhauled CloudCheck from the ground up to solve each of these problems, resulting in faster, more accurate, and more comprehensive detection across numerous cloud providers.
CloudCheck
CloudCheck is an open-source cloud signature database, CLI tool, Python library, and Rust library. As of January 2026, it supports 56 cloud providers (see here for an up-to-date list).
JSON Signatures
CloudCheck’s signatures are updated daily via an automated CI/CD pipeline, which cleans, dedupes, and defrags all the data before saving it to a JSON file on GitHub. This file is free to download and parse, and useful if you like to do things manually instead of using the convenient CLI and API wrappers.
Unique Data Sources
CloudCheck leverages several unique methods to stay up-to-date automatically.
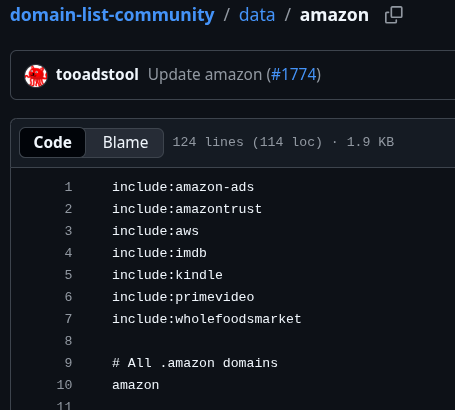
For domains, instead of hardcoding domains like “amazonaws.com”, it pulls daily from domain-list-community. This not only helps to keep the domain lists up-to-date and avoids manual maintenance, but also enables detection of child entities — for example, Kindle and Audible domains nested underneath Amazon:
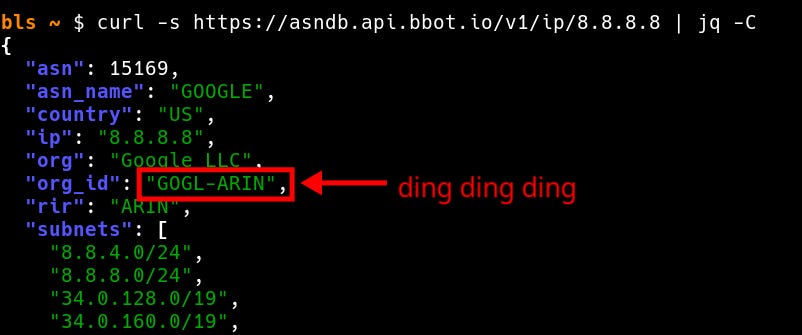
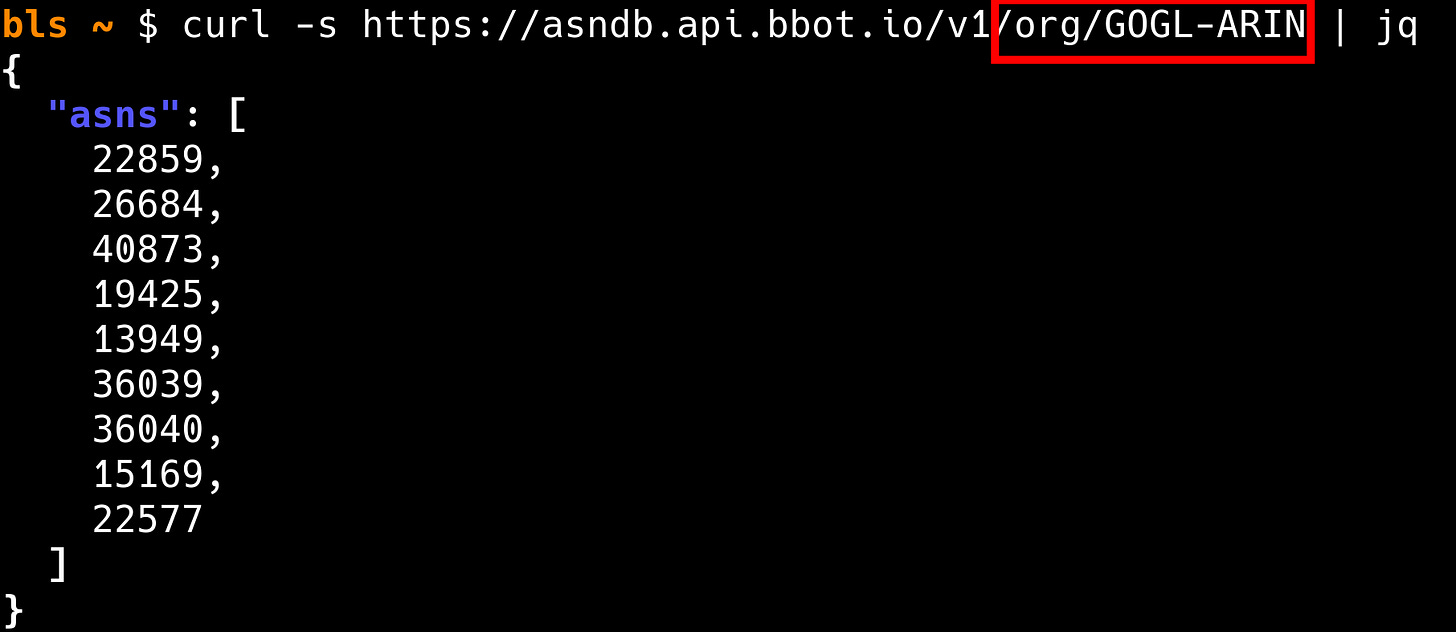
For IP addresses, instead of hardcoding CIDRs or ASN numbers, organizations are tracked by their Internet Registry IDs. This means CloudCheck can detect brand-new ASNs as they’re spun up, even before they’re announced to the public.
The secret ingredient here is ASNDB, which is queried during the daily signature update. ASNDB is our very own REST API, and part of a soon-to-be-announced API Suite with a generous free tier.
Convenient Categories
Cloud providers are sorted into categories like “cloud”, “cdn”, “waf”, “gov”, etc.
Installation
CloudCheck is written in Rust and installable with one command:
cargo install cloudcheckUsage - CLI
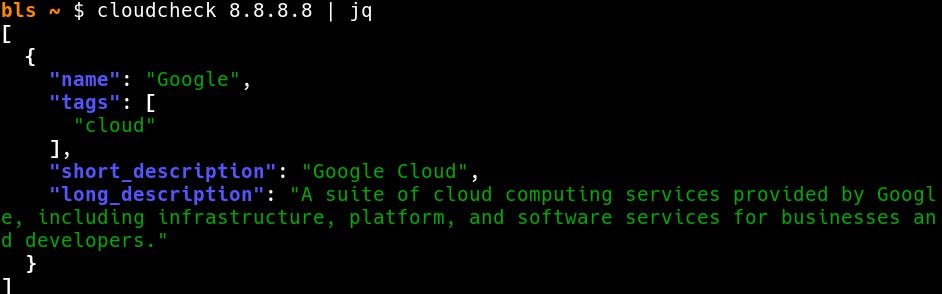
CloudCheck’s CLI is simple to use. Just execute CloudCheck followed by the hostname or IP you want to look up.
cloudcheck <hostname or ip>Output is JSON:
Let us know on Discord or Github which features you want added to the CLI!
Usage - Python API
# installation
pip install cloudcheckimport asyncio
from cloudcheck import CloudCheck
async def main():
cloudcheck = CloudCheck()
results = await cloudcheck.lookup(”8.8.8.8”)
print(results) # [{’name’: ‘Google’, ‘tags’: [’cloud’]}]
asyncio.run(main())Usage - Rust API
# Add to Cargo.toml
[dependencies]
cloudcheck = “9.2”
tokio = { version = “1”, features = [”full”] }use cloudcheck::CloudCheck;
#[tokio::main]
async fn main() {
let cloudcheck = CloudCheck::new();
let results = cloudcheck.lookup(”8.8.8.8”).await.unwrap();
println!(”{:?}”, results); // [CloudProvider { name: “Google”, tags: [”cloud”] }]
}Usage - REST API
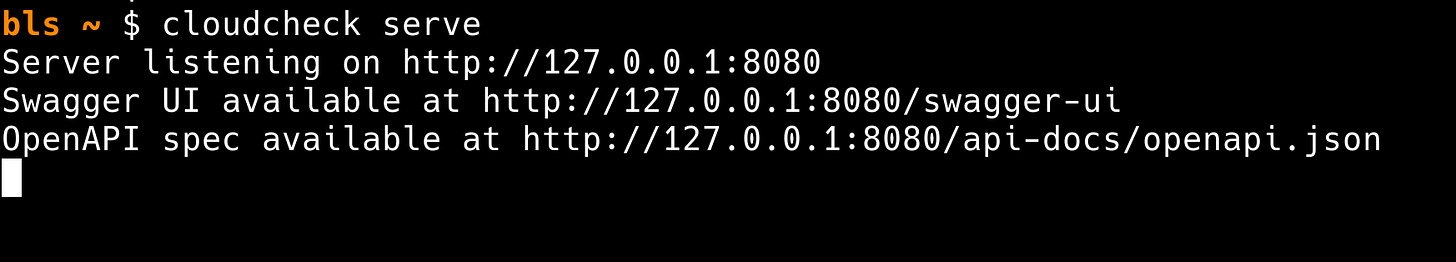
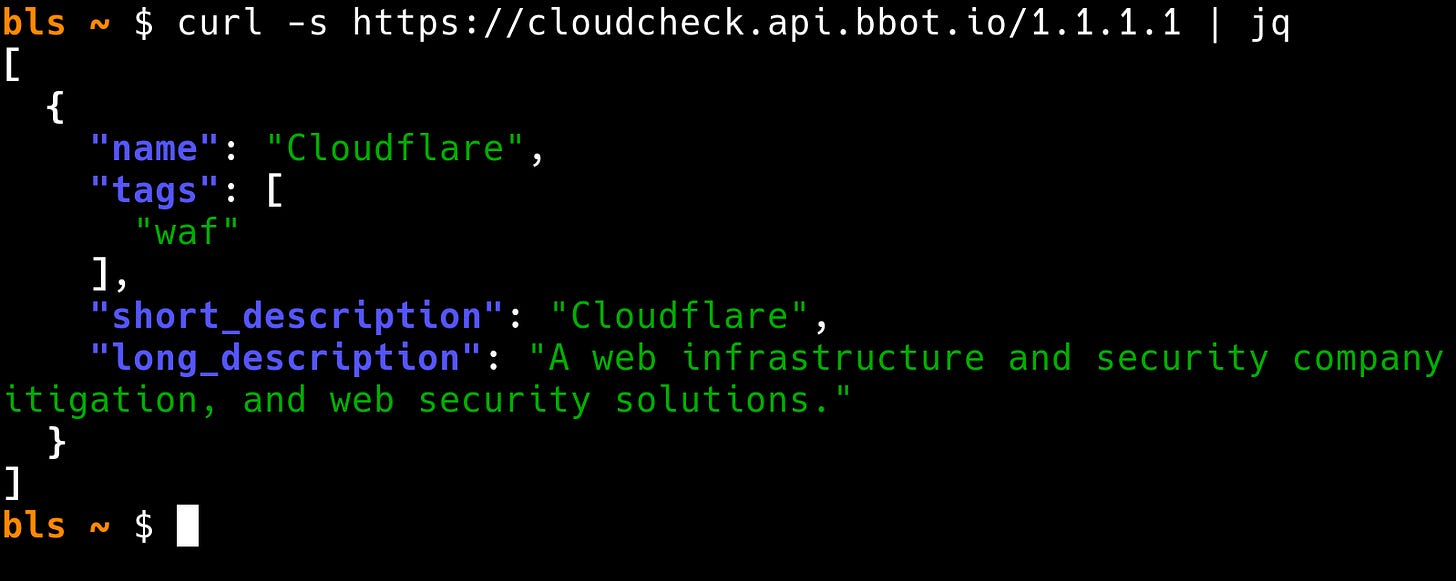
CloudCheck’s CLI and code libraries perform their lookups against a local in-memory database, which can also be served as a REST API:
We’ve deployed this at cloudcheck.api.bbot.io. You can try it out for free at 10 requests/minute:
Conclusion
We hope you find CloudCheck useful. It is only a small part of the growing BBOT ecosystem - an open-source framework for recursive asset discovery and reconnaissance.
To fully leverage this tech stack and our expert team of analysts and researchers, contact us to learn more about our Enterprise ASM Offering.
Happy hacking!


Impressive approach to cloud detection automation. The registry ID tracking instead of hardcoded ASNs is kinda genius for catching new infrastructure befor it's even public. Been burned too many times by stale CIDR lists in pentests where targets had shifted to new ranges.