The BLS-Bible
A knowledge-base management tool aimed to improve the lives of information security professionals in all walks of life.
At Black Lantern Security (BLS), we have felt the pains of managing the vast sea of knowledge acquired by each of our amazingly talented operators. We have tried Wikis, Git repositories, and decentralized collections of data in CherryTree or Obsidian - all in an attempt to manage everything. Each option we tried had their drawbacks and some features we loved. After a great deal of thought and planning, (with a herculean effort from @ThomasPresto1 on many of the guides and the CLI) as well as front/back-end development from @codymartin, BLS is thrilled to announce the public release of the BLS-Bible!
Feature Set
For starters, the BLS-Bible is packed with features:
Multiple deployment types to suit your operational needs
Markdown rendered pages
In-app editing
Tag-based, filterable searching
Regular expression searching with optional context
Threat profiles
Exportable to PDF, ATT&CK Navigator
Calculate percent-match to known APTs
MITRE ATT&CK mapping for guides via tags
Version control thanks to Git
Apochrypha - Git sub-modules so you can pull in your favorite repositories of knowledge
Assessalonians - Git sub-module specifically for your organization’s private repository of knowledge
Apostles - A leaderboard to rank the entire community’s contributions to the BLS-Bible
Developer tools - A collection of utility functions to help maintain the knowledge-base
Themes - Easily switch between premade color schemes or make your own
Instead of writing at length about each of these, it is easier to demonstrate with images.
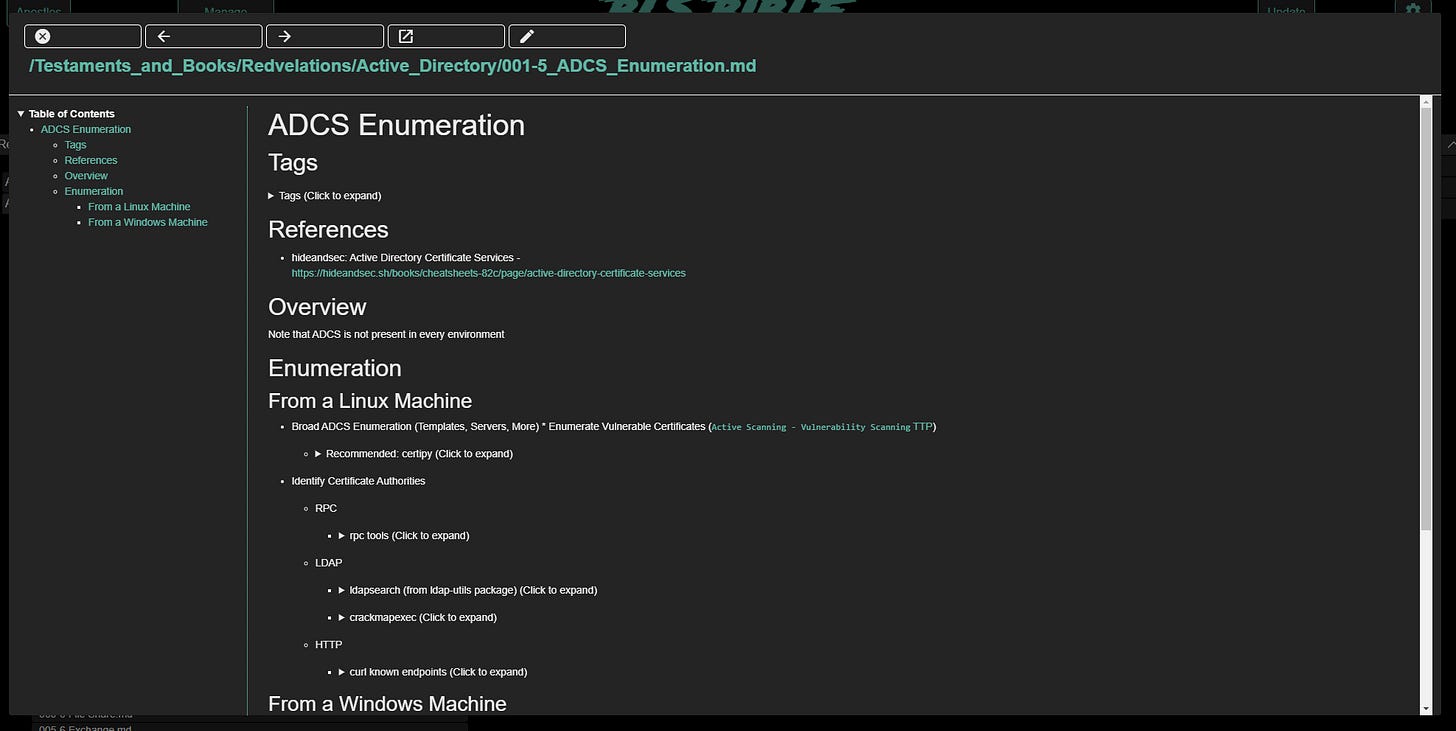
Markdown Rendering
All files under the /Data directory can be rendered to screen in a human readable format. This includes programs/scripts as well with full syntax highlighting. The reading window has the table of contents on the left pane and has custom history management as well as navigation at the top. Clicking a link within the page will take you to that page. The arrow buttons allow you to traverse forward and backward through your reading.
In-App Editing
On specific deployments (dev, ops) you can edit pages within the application itself. The syntax and functionality available are nearly equivalent to what you’d expect when using GitHub. If you want to make a quick edit on your local system or deploy a temporary ops server to edit on collaboratively during an assessment, you can. Once you’re ready to push your content additions, you can commit your changes to a new branch and request a pull into the development branch.
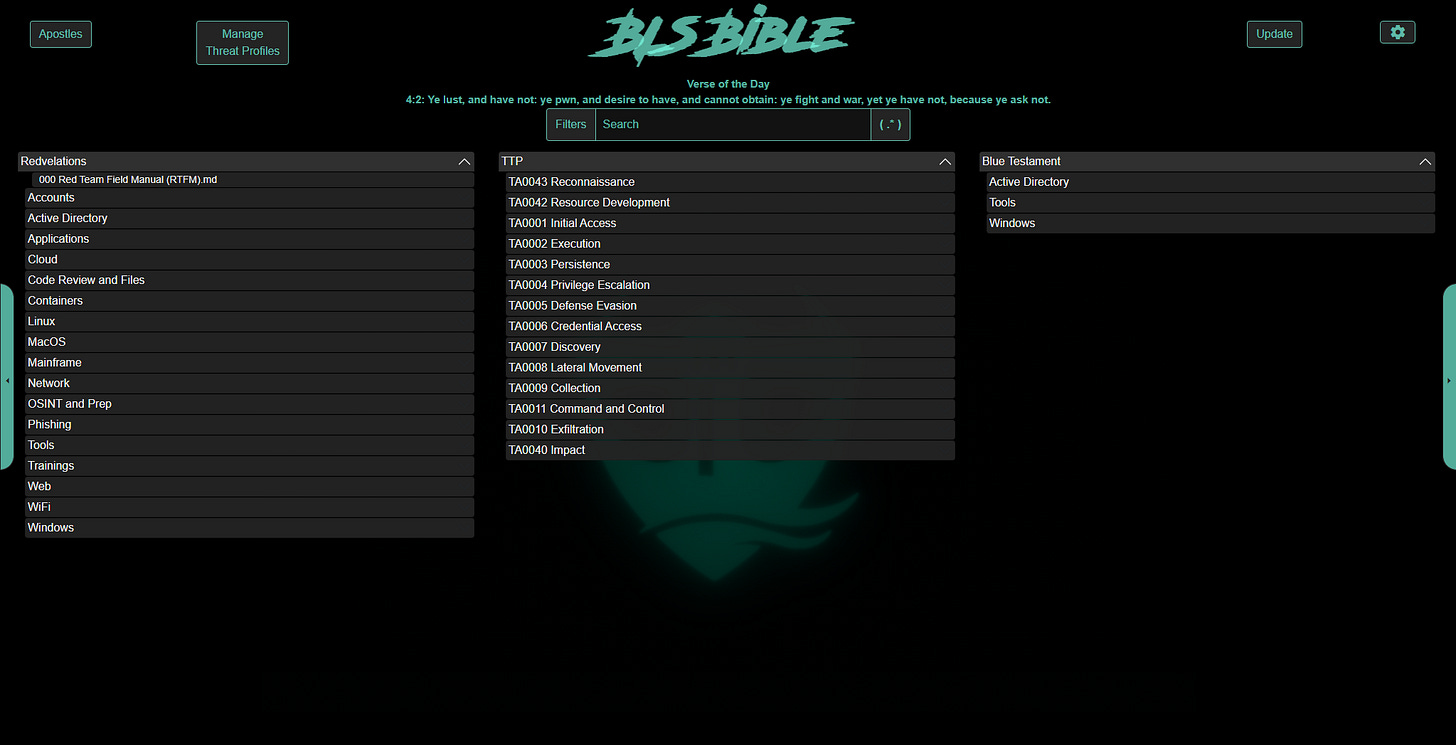
Tag-Based, Filterable Searching
The basic search functionality is built around tags (#@tag) that are included within each page, as well as the naming of the folders and pages themselves. These tags are indexed to provide a very responsive list of results.
You can further filter down the results shown to you in your search results, as well as the main screen. Selecting these filters will show you those resources containing the relevant tags. Selecting known threat profiles will filter to the techniques associated with the threat profiles.
As you can see above, according to MITRE’s data, APT41 is known utilizing the listed techniques, and those techniques happen to contain AD.
Regular Expression Searching with Context
While tagging is helpful, not everything is going to be tagged perfectly. Additionally, we include content from other amazing public projects and can’t expect them to adhere to our tagging system. For those reasons, you can also perform a regex or advanced search for the thing you’re looking for. This will take a regex pattern and search through every file within the project (including external projects) and provide you with a list of files containing the pattern match. You can also bump up the context setting to see for sure if that’s the file you are looking for.
Threat Profiles
It made sense to allow end users the ability to create their own threat profiles within the application. With threat profiles, you can add techniques to your custom threat profile as you proceed through your assessment. At the end of your assessment, you’ll have a list outlining the techniques you used against the target environment.
Exporting Threat Profiles
If your client is interested in learning more about the techniques used, you can export the threat profile directly to a PDF document that you may share with your client.
You can also export your profile or profiles directly to an ATT&CK Navigator file to be ingested into this widely-used application.
Matching Threat Profiles to APTs
Another helpful feature is the ability to compare your custom threat profiles to known advanced persistent threats (APTs) as tracked by MITRE. This gives you an idea of how well you are emulating known attackers.
MITRE ATT&CK
Since we are including the MITRE ATT&CK framework into the application, it also made sense to give a visual representation of what techniques each guide was employing. This is handled through placing tags within the guide for the individual techniques being used.
Additionally, if you are trying to recreate a specific ATT&CK technique, it is helpful to quickly see which guides you can use to help you execute your actions.
This isn’t just restricted to offensive security. While the Blue Testament isn’t well built out currently, the goal is to have full coverage for offensive and defensive security professionals alike. With greater contributions to the Blue Testament, we will start to see overlap (in purple, of course) in the tactics, techniques, and procedures (TTPs) where we have mapped both the offensive and defensive strategies.
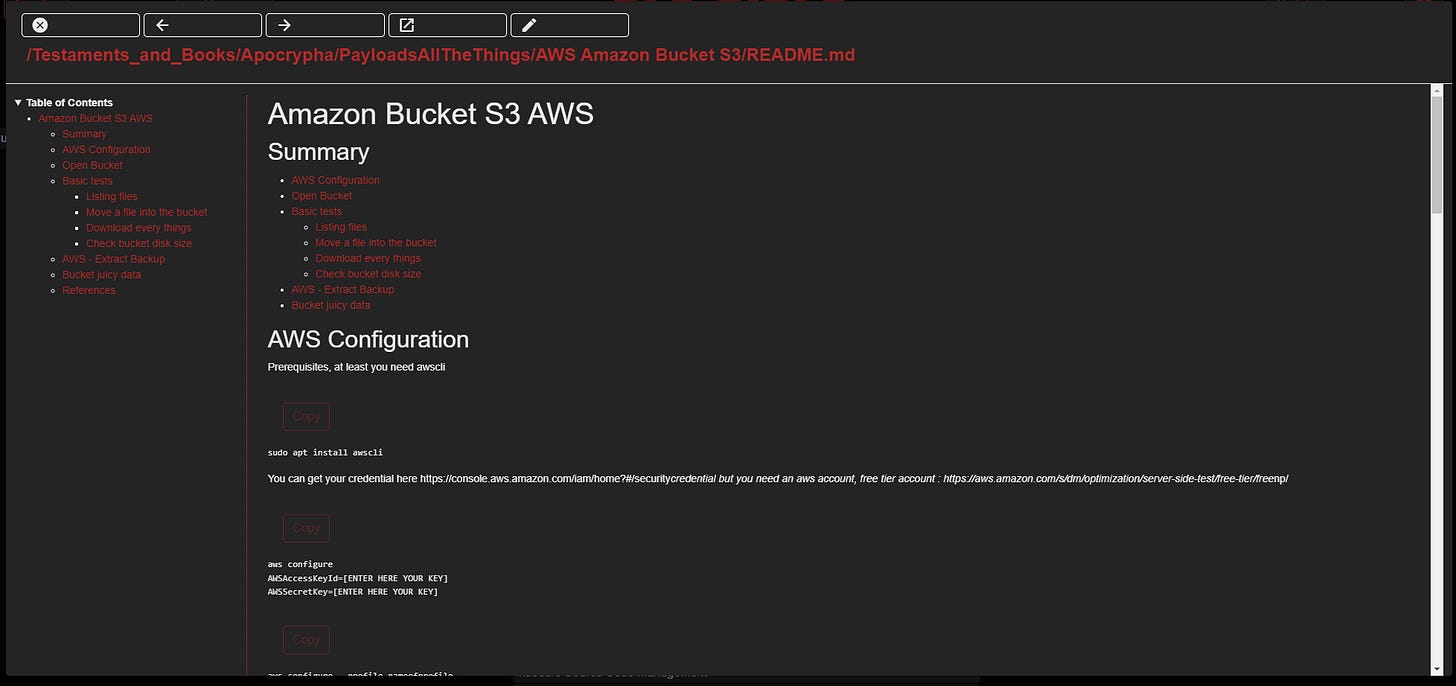
Apocrypha
It is not our goal to reinvent the wheel or reproduce what is already out there. At the same time, we want to make sure we have access to the materials we rely on as security researchers. For these reasons, we’ve included Apocrypha which utilizes Git sub-modules to pull in high-value repositories like PayloadsAllTheThings and HackTricks. If you stand this up on your own attack box or op-specific server before entering an unknown network, you will be sure that you will have all the resources you need to get the job done.
We take advantage of the fact that most (if not all) knowledge-base repositories are written using Markdown. This allows us to render their contents in the same way as our own content.
Apostles
To give everyone their fair shake and some public bragging rights, we included the Apostles. This is a leaderboard that ranks contributors to the project based on the number of pull requests submitted, and the number of files changed. This feature will require you to use your own GitHub API key (public read-only) to properly function. We hope this becomes a fun way to add some competition into spreading quality knowledge throughout the community.
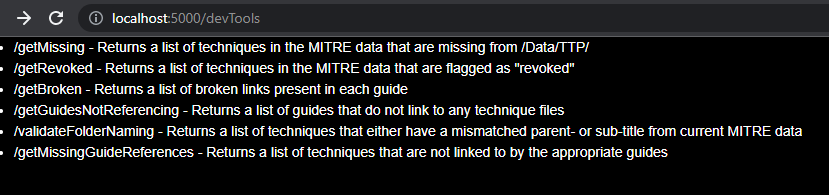
Developer Tools
This block of features is primarily aimed at those who want to help maintain the repository. The endpoints are only accessible on dev deployments but will give you quick readouts for things that may need to be addressed or updated as the project continues to grow in content.
Themes
Lastly, what is a good application without some ability to change how it looks. Included are five dark mode themes that can easily be switched between. Thanks to the simple way the colors are defined, it is very easy to create your own custom themes and have them submitted for general use.
For the Community
We sincerely hope this tool finds those who are experiencing the same pains we were without knowledge-base management. We welcome contributions and suggestions to the project at the GitHub repo (one more time in case you missed it). Please feel free to reach out to anyone at BLS with any questions or ideas you may have about the project on our Discord server or directly over Twitter (@codymartin, @blacklanternllc).